At the end of the 1990s, Israel found its methods of surveillance outdated and not suited to the craft of their enemies.
Their enemies were everywhere, more determined, innovative and increasingly menacing from Hezbollah in Lebanon, Iran, Libya, to Hamas in Gaza and Amman.
Consequently, Ami Ayalon established more modern techniques.
THE SHIN BET WAS the first of the intelligence agencies to regain its footing. Its chief, Ami Ayalon, and the inquiry panels he set up to find out what had gone wrong reached the conclusion that the Shin Bet had become weak and ineffective in two of its main areas of activity. The first was the acquisition of information. For decades, the Shin Bet had relied upon intelligence obtained from human sources, but this reservoir had almost dried up. No substitute had yet been found for the hundreds of Palestinian agents that it had lost when Israel withdrew from Palestinian territory after the Oslo Accords. The Shin Bet failed to develop alternative methods and was unable to recruit agents inside Hamas, an ideological-religious movement whose members were less likely to be tempted by bribes. One of the Shin Bet inquiry panels put it succinctly—and damningly: “The organization is not attuned to the environment it works in.” The second inadequacy was what the Shin Bet did with information once it was obtained. Ayalon visited the organization’s archives and stared incredulously at the huge containers stuffed with hundreds of thousands of cardboard binders. “We are behaving like a medieval organization,” he told the senior command forum of the Shin Bet. “An archive like this does not make it possible to construct a real-time intelligence picture. Even if all the information were to be found in the files, it wouldn’t help us at all.” Ayalon declared that “the Shin Bet is not an intelligence body, but rather a preventive body.” In other words, the agency’s purpose was not merely to gather information for the sake of collection, but rather to thwart the enemy’s intentions in real time. In order to do so, the Shin Bet had to collect intelligence and analyze it in the briefest of time spans. Ayalon argued that the solution was to be found in advanced technologies. Tech-based sources would replace human sources, producing a multi-dimensional, real-time intelligence picture.
In 1996, these were revolutionary thoughts that generated a crisis of confidence in the Shin Bet, drew harsh criticism of Ayalon, and even led many to quit the agency. But Ayalon stuck to his guns. He created a number of new teams and departments that developed cutting-edge techniques for collecting information: penetrating various data systems and intercepting emails, phone calls, and, later on, social media communications. They also developed new ways to use the information: state-of-the-art techniques for analyzing vast amounts of data and extracting the most important bits of intel. Ayalon and his tech teams shifted the focus of the Shin Bet so that more emphasis was placed on the connections between people—more emphasis on the network, rather than on each separate individual.
The Shin Bet was the first to grasp the huge potential of tracking mobile phones, first through the phone calls themselves and later through geolocation, texting, video transmissions, and online surfing. Under Ayalon, the agency’s entire operational structure changed. It no longer relied on regional case officers, deployed geographically, who ran agents and functioned more or less independently, but instead concentrated activities around a “desk,” whose personnel sat at computer monitors, gathering information, piecing it together, and ordering operatives to gather missing pieces of the puzzle. The makeup of Shin Bet’s personnel was also changing rapidly. Many of the agency’s old case officers left, while young men and women from the IDF’s tech units were being recruited at a quick pace. Soon, 23 percent of the agency’s personnel were operatives trained extensively in the development of innovative technologies. “We set up an entire division of Q’s,” said Diskin, referring to the tech wizard of James Bond movies. “In it, dozens of amazing startups are under way simultaneously.”
………….Diskin, in the Shin Bet, and Yaalon, in the military, had to shatter quite a few entrenched bureaucratic procedures and navigate various interpersonal difficulties to get everyone into the second-floor space of the Jerusalem Shin Bet headquarters, which would now be called, appropriately, the Joint War Room (JWR). Especially tough was the resistance of 8200, the glamorous SIGINT unit of AMAN, who tried to insist that Shin Bet come to them instead. On December 11, 1999, everything was ready for action……………In September 2000, two months after Diskin had been appointed deputy director of the Shin Bet and Yaalon had been named deputy chief of the IDF General Staff, the two recommended that the model they had developed for the Central Command region be replicated for the entire country—that a permanent war room be set up for implementing major operations and targeted killings. The proposal was accepted, and space was set aside inside a building under construction at the Shin Bet HQ, in north Tel Aviv. The timing was fortuitous. “If we had not implemented the technological revolution and hadn’t set up the special war room,” Diskin said, “it’s doubtful whether and how we would have coped with the huge challenge that was posed for us by the Second Intifada.”
From Ronen Bergman’s book, “Rise and Kill First”
Let us consider the state of the art of PC business computing (software dominated by Microsoft) since the 1990s by looking at this link:
https://microsoft.fandom.com/wiki/Timeline_of_Microsoft_products
So in 2000, the latest operating system was Windows ME.
If we read about the timeline of the 9/11 attack we find:
The hijackers began entering the United States in January 2000 to advance the plot. All 19 were in the country by early July 2001.
https://www.fbi.gov/history/famous-cases/911-investigation
The rise of terrorism grew as the rejection of the support for a sovereign state of Israel was placed in the Middle East region.
There are clear signs that state sponsorship of terrorism is declining. During the 1980s and the early 1990s, Iran and terrorist groups it sponsors were responsible for the most politically significant acts of Middle Eastern terrorism. Although Iran continues to actively sponsor terrorist groups, since 1997 some major factions within Iran have sought to change Iran’s image to that of a more constructive force in the region. Pressured by international sanctions and isolation, Sudan and Libya appear to have sharply reduced their support for international terrorist groups. Syria, according to the Administration, has made a strategic choice for peace, implying that Syria may be ready to expel terrorist groups in areas under its control if there is a peace agreement with Israel.
The major state sponsors are, to some extent, becoming eclipsed by the radical Islamic terrorist network of exiled Saudi dissident Usama bin Ladin, who is independently financed and enjoys safe haven in Afghanistan. The goals of bin Ladin and his cohorts are to oust pro-U.S. regimes in the Middle East and gain removal of U.S. troops from the region. Within the past year, there have been growing signs that bin Ladin might be seeking to disrupt the Arab-Israeli peace process; bin Ladin cells have been discovered and their members arrested by authorities in Jordan and Lebanon, although no attacks linked to bin Ladin were actually carried out in these countries.
The Arab-Israeli peace process is a longstanding major U.S. foreign policy initiative, and the Administration and Congress are concerned about terrorist groups and state sponsors that oppose the process. Since the 1980s, Islamist groups such as Hamas and Palestinian Islamic Jihad have largely displaced secular, nationalist groups as the most active anti-Israel organizations. However, possible because of greater anti-terrorism vigilance by the Palestinian Authority (PA), these groups have been less active against the peace process over the past year. Some Hamas leaders are moving toward cooperation with PA Chairman Yasir Arafat in shaping a final peace settlement with Israel.
U.S. counterterrorism policy has generally been directed against state sponsors, which are readily identifiable targets. A problem for U.S. policy has been how to coordinate U.S. counterterrorism policies with those of U.S. allies. Most allied governments believe that engaging these countries diplomatically might sometimes be more effective than trying to isolate or punish them. The Administration and Congress have tended to rely more on economic and political pressure against state sponsors in an effort to make them more cautious. In 1998, the Administration has, to some degree, attempted to reward gestures by state sponsors to distance themselves from international terrorism. At the same time, the Administration and Congress have stepped up efforts to directly pressure terrorists and terrorist groups. U.S. missile strikes on bin Ladin s network on August 20, 1998, in retaliation for the bombings of U.S. embassies in Kenya and Tanzania two weeks earlier, suggests that military action is still considered a viable component of U.S. efforts to combat individual terrorist groups.
https://www.globalsecurity.org/security/library/report/crs/crsterr3.htm

2003:
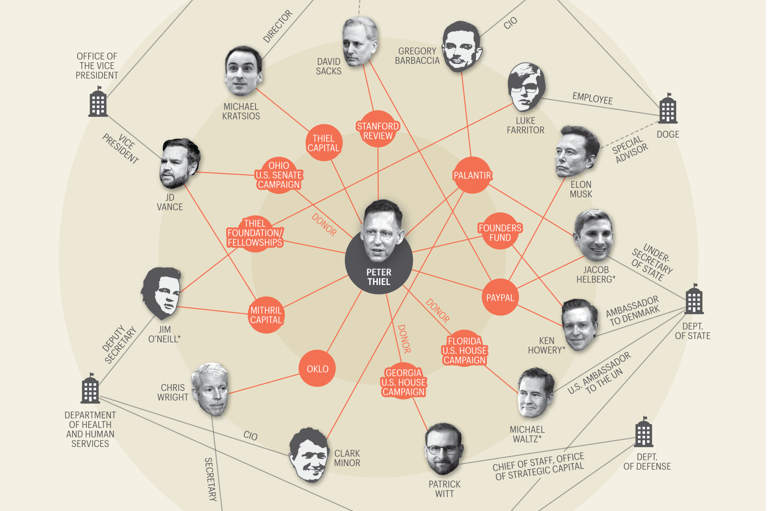
Palantir was founded in 2003 with a mission to help intelligence agencies make better use of their data securely and responsibly. Today, governments around the world use Palantir Gotham and Palantir Foundry to understand and defend against evolving threats to national security, from cyberattacks, to disinformation, to insurgencies.
Israeli Forces use Palantir:
Two weeks ago, Alex Karp, co-founder and CEO of software company Palantir Technologies (NYSE: PLTR), landed in Israel. Palantir was borne aloft by the growing trend of Big Data, years before OpenAI and similar companies arrived on the scene.
Karp, a Jewish resident of Silicon Valley, came to a public event at Tel Aviv University, and in a hall packed with students, journalists, and tech workers, mainly spoke about entrepreneurship and technology, but also showered praise on Israel.
In recent years, Palantir has become one of the most intriguing contractors of Israel’s security forces. The fact of such cooperation is no secret: immediately after his appearance at the university, Karp travelled to military headquarters in Tel Aviv, where he signed an upgraded agreement with the Ministry of Defense, and was even photographed with Danny Gold, head of the Israeli Directorate of Defense Research & Development (DDR&D), who became well known as the manager of the development of the Iron Dome missile defense system.
https://en.globes.co.il/en/article-What-is-Palantir-doing-in-Israel-1001468876
And Palantir will flourish under the Trump administration;
Data-mining company Palantir is poised to turbocharge its sales to the U.S. military under President Donald Trump, amid signs that his administration plans to loosen the hold of traditional defense contractors and tap Palantir executives for key government positions.
But Palantir has also been laying the groundwork for a much deeper infiltration of Washington, building a sprawling influence network designed to secure government business for years to come, a new Tech Transparency Project (TTP) investigation has found.
TTP found that Palantir’s hiring of government officials is more extensive than previously reported, with the company stocking up on veterans of the White House, Defense Department, CIA, and Congress. The investigation also identified a robust revolving door between Palantir and the Pentagon office tasked with integrating commercial technology into military operations—a unit critical to Palantir’s government sales.
Over the past several years, Palantir has dramatically increased its lobbying budget, in one quarter even surpassing the spending of longtime “Beltway bandit” defense contractor Northrop Grumman, the investigation found. At the same time, Palantir is investing in soft influence efforts, establishing a non-profit foundation that seeks to shape D.C. policy discussions in the company’s favor through academic papers, conferences, and public commentary
https://www.techtransparencyproject.org/articles/inside-palantirs-expanding-influence-operation
Note: Oracle integrates Palantir Foundry for clients using tenancy segments in its Cloud operations.
https://docs.oracle.com/en/solutions/palantir-foundry-ai-platform-on-oci/index.html
Oracle founder,Larry Ellison, funds Tony Blair’s Foundation in the UK which has focused on assisting the UK in digitising health records and other major data sources in the UK.
It is interesting to read the Timeline of Oracle, which goes back to 1977.
https://populartimelines.com/timeline/Oracle-Corporation/full
JULY 2025, re: Trump Aministration
According to The New York Times, Palantir corporation’s software will be used to combine data gleaned from the Department of Homeland Security, the Department of Defense, the Department of Health and Human Services, the Social Security Administration, and the Internal Revenue Service. Meanwhile, the administration wants access to citizens’ and others’ bank account numbers and medical claims.

You must be logged in to post a comment.